Over the past several years, Apple has emerged as a company that deeply cares about privacy. Apple’s Security Bounty program is designed to fix security issues and reward the researchers. A security researcher has penned down his thoughts on Apple Security Bounty and his overall experience. Apple allegedly refused to pay a bounty for a critical bug that qualifies for the Apple Security Bounty program.
Location Tracking Vulnerability
Security researcher Nicolas Brunner found a way to access users’ locations permanently. He was able to do so without the need for user permission. The exploit worked on any iOS 13 or older device. Brunner reported the issue, and it got accepted. Soon enough, Apple fixed the exploit on iOS 14. Apple not only fixed the bug but also credited Brunner on the iOS 14 security content release notes.
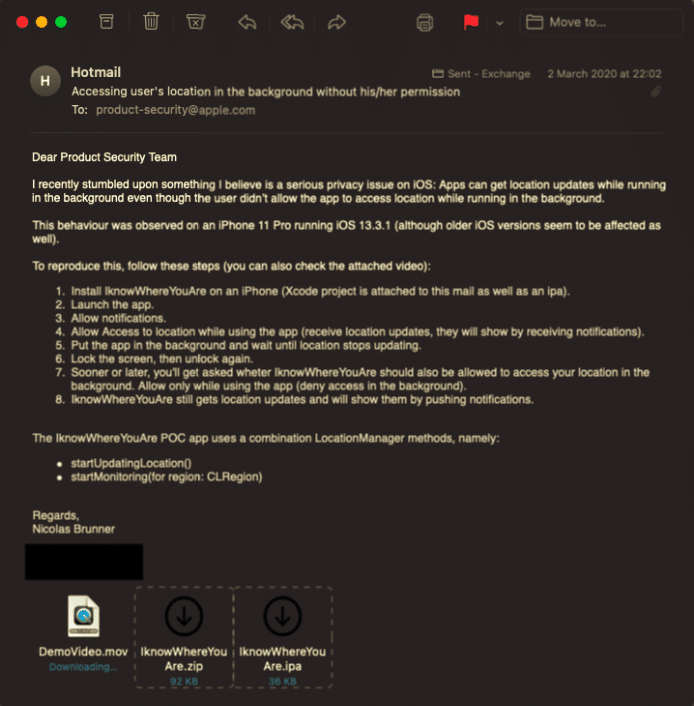
Brunner was working on a project when he stumbled upon the bug. He was able to permanently access the device location without the need for any permission. In other words, an attacker can potentially track your location even if the app is in the background. The security researcher submitted proof of concept to the security bounty program.
A week later, Apple responded to Brunner, and it took them six months to fix the issue via a security update. The company duly credited Brunner’s finding and his name features on the security advisories of iOS 14. For the next eight months, Brunner repeatedly asked Apple for the security reward bounty. It looks like Apple ignored the request for close to a year. One fine day, Brunner got an email from Apple that said the issue doesn’t qualify for the Apple Security Bounty. Apple stopped responding to further emails from Brunner.
Our Take
It is not the first time Apple’s Security Bounty has been criticized. Previously, famed security researcher Ian Beer alleged that Apple had not paid bounty rewards amounting to an nearly $2.45M. He further challenged Apple to donate the money to Amnesty International; a charity focused on human rights.
As a privacy focussed company, Apple seems to be doing very little to encourage bug hunters. Zero-day exploits are worth millions in the black market, and Apple is indirectly dissuading security researchers by not paying the bounty. Meanwhile, companies like NSO thrive on such exploits and allegedly help governments with state-sponsored attacks.
[via Nicolas Brunner, Ian Beer]