On Sunday evening, a hacker posted photographs to 4Chan, which showed dozens of celebrities in compromising positions.
The Next Web is now reporting that the massive celebrity photo leak could have been due to a security breach in Apple’s iCloud service.
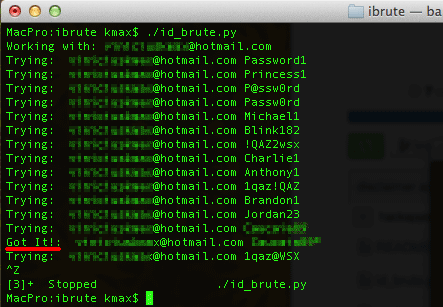
The hacker seems to have used a brute force attack to gain access to the celebrity’s Apple ID account. In a brute force attack, the malicious could use a script to repeatedly guess the password till it discovers the correct one. The brute force method are usually successful in cases where the victim has used a weak password.
Earlier today, a hacker posted a Python script called iBrute on GitHub, which allows malicious users to brute force a target account’s password on Apple’s iCloud. It is not clear if the same script was used for the security breach.
The vulnerability allegedly discovered in the Find my iPhone service appears to have allowed attackers to use this method to guess passwords repeatedly without any sort of lockout or alert to the target. Once the password has been eventually matched, the attacker can then use it to access other iCloud functions freely.
Ideally, the service should have disabled the account temporarily when the wrong password was entered repeatedly to protect the victim’s account, but it looks like Apple wasn’t doing it for the Find my iPhone service. Apple appears to have patched the vulnerability at 3:20 am PT, as The Next Web reports that it is now locking the account after five unsuccessful attempts. The hacker of iBrute has also confirmed that Apple has patched the vulnerability.
Apple is yet to comment on the incident. It again highlights the importance of using a strong password for your online accounts, and enable two-step authentication for services like iCloud that offer it, to avoid such incidents.
Update:
Apple has issued a statement to Re/code that is actively investigating the celebrity photo hack.
[via The Next Web]