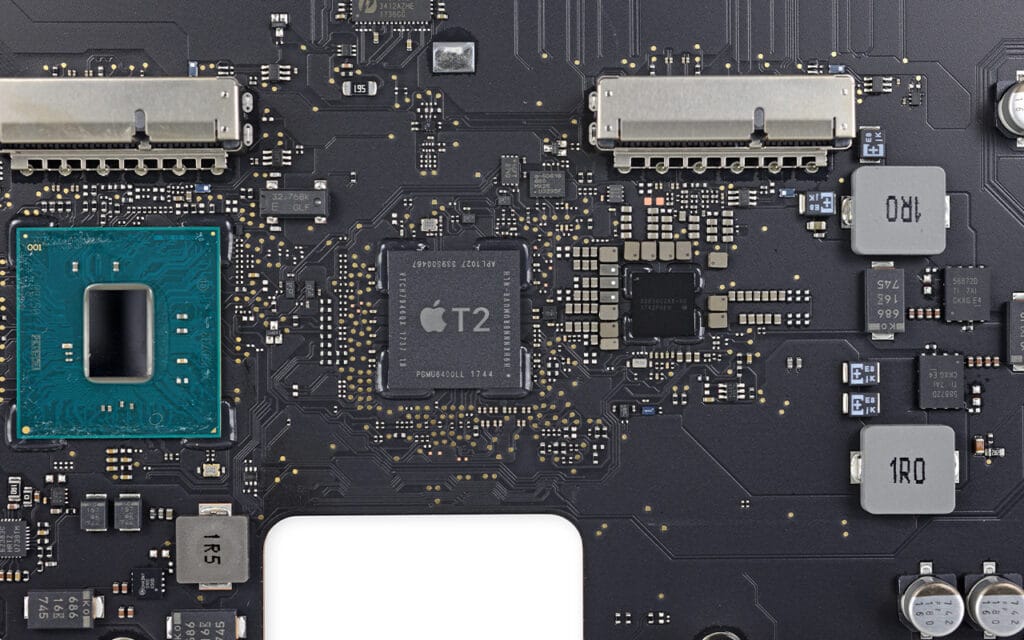
A newly-discovered vulnerability affects macOS systems with the Intel processor and T2 chip. The cybersecurity researcher who unearthed the vulnerability says it is not patchable and can potentially give root access to attackers.
Most of the new MacBook’s come with a T2 security chip designed by Apple. It is based on an A10 ARM processor and is tasked with select functionalities like audio processing, handling I/O, and partaking as a hardware security module. Furthermore, the T2 runs on bridgeOS, which is updated every time you update your Mac.
The exploit is called check8 and was developed initially for iPhone X. Interestingly, the iPhone X is powered by A10 processor, and the T2 chip is also modeled after the A10 processor. Typically, the T2 chip throws a fatal error whenever it gets a decryption call. However, the attackers can circumvent the check with the help of a blackbird vulnerability. The worst part is that sepOS/BootROM is Read-Only memory, which means Apple will not be able to patch this without changing the hardware.
The good news is that attackers will require physical access to the system and use devices like malicious USB-C cable or any other hardware insert. Moreover, the vulnerability can be for bypassing security locks and built-in Activation Lock manually. Access to T2 will grant the attacker access to full kernel execution privileges. Disk encryption can prevent the attack to a certain extent. However, attackers can gain access to keyboards by injecting keyloggers in the T2 firmware.
How Does it affect macOS users?
The security researcher says the vulnerability can bypass multiple levels of access. The attacker can potentially bypass the activation lock, allowing macOS devices to be unlocked and sold in the black market. Mac users are advised to use Apple Configurator to reinstall bridgeOS on T2 Chip and, most importantly, dont leave your device unattended. Never plug in an unknown USB device.
